Understanding Internet Protocols: HTTP, HTTPS, TCP, UDP, WebSocket, SMTP, and FTP
In today's interconnected world, the internet is an indispensable part of our daily lives. From browsing websites to sending emails and streaming videos, countless activities rely on a complex web of rules and procedures known as internet protocols. These protocols are the unsung heroes that ensure data travels efficiently and securely across networks. This article will demystify some of the most common and crucial internet protocols, explaining their roles, how they differ, and why they are essential for modern digital communication.

1. HTTP (Hypertext Transfer Protocol)
HTTP, or Hypertext Transfer Protocol, is a foundational protocol for data communication on the World Wide Web. It operates as a simple request-response protocol, typically running over TCP. HTTP defines how clients (like web browsers) send messages to servers and how servers respond. Both request and response headers are in ASCII format, while the message body often follows a MIME-like structure. This straightforward model was a key factor in the early success of the web, making development and deployment remarkably simple and direct.

2. HTTPS (Hypertext Transfer Protocol Secure)
HTTPS, or Hypertext Transfer Protocol Secure, is the secure version of HTTP. It provides a secure channel over an insecure network by adding a layer of encryption and authentication on top of HTTP. This security is primarily achieved through the use of SSL (Secure Sockets Layer) or its successor, TLS (Transport Layer Security). HTTPS operates on a different default port than HTTP and includes an encryption/authentication layer between HTTP and TCP. This system ensures data integrity and confidentiality, making it widely used for sensitive communications on the World Wide Web, such as online banking and e-commerce transactions.

3. WebSocket
WebSocket is an independent protocol built on top of TCP, designed for full-duplex communication over a single TCP connection. It establishes a connection through an HTTP/1.1 101 Switching Protocols handshake. This handshake process, initiated by the browser and responded to by the server, upgrades the HTTP connection to a WebSocket connection. Once established, the WebSocket connection allows for persistent, bidirectional communication between a client and a server, making it ideal for real-time applications like chat applications, online gaming, and live data feeds, where continuous data exchange is crucial.

4. TCP (Transmission Control Protocol)
TCP, or Transmission Control Protocol, is a core protocol of the internet protocol suite. It is specifically designed to provide reliable, ordered, and error-checked delivery of a stream of bytes between applications running on hosts in an unreliable interconnected network. TCP achieves this reliability through mechanisms like sequence numbers, acknowledgments, retransmission of lost packets, and flow control. It is a connection-oriented protocol, meaning a connection must be established between the sender and receiver before data can be exchanged. This makes TCP suitable for applications where data integrity and guaranteed delivery are paramount, such as web browsing (HTTP/HTTPS), email (SMTP, IMAP), and file transfers (FTP).
5. UDP (User Datagram Protocol)
UDP, or User Datagram Protocol, is a connectionless, unreliable, and datagram-based transport layer communication protocol. Unlike TCP, UDP prioritizes speed and efficiency over reliability. It does not establish a connection before sending data, nor does it guarantee delivery, order, or error-checking of packets. This makes UDP suitable for applications where real-time performance is critical and occasional data loss is acceptable, such as streaming video, online gaming, and Voice over IP (VoIP).
6. SMTP (Simple Mail Transfer Protocol)
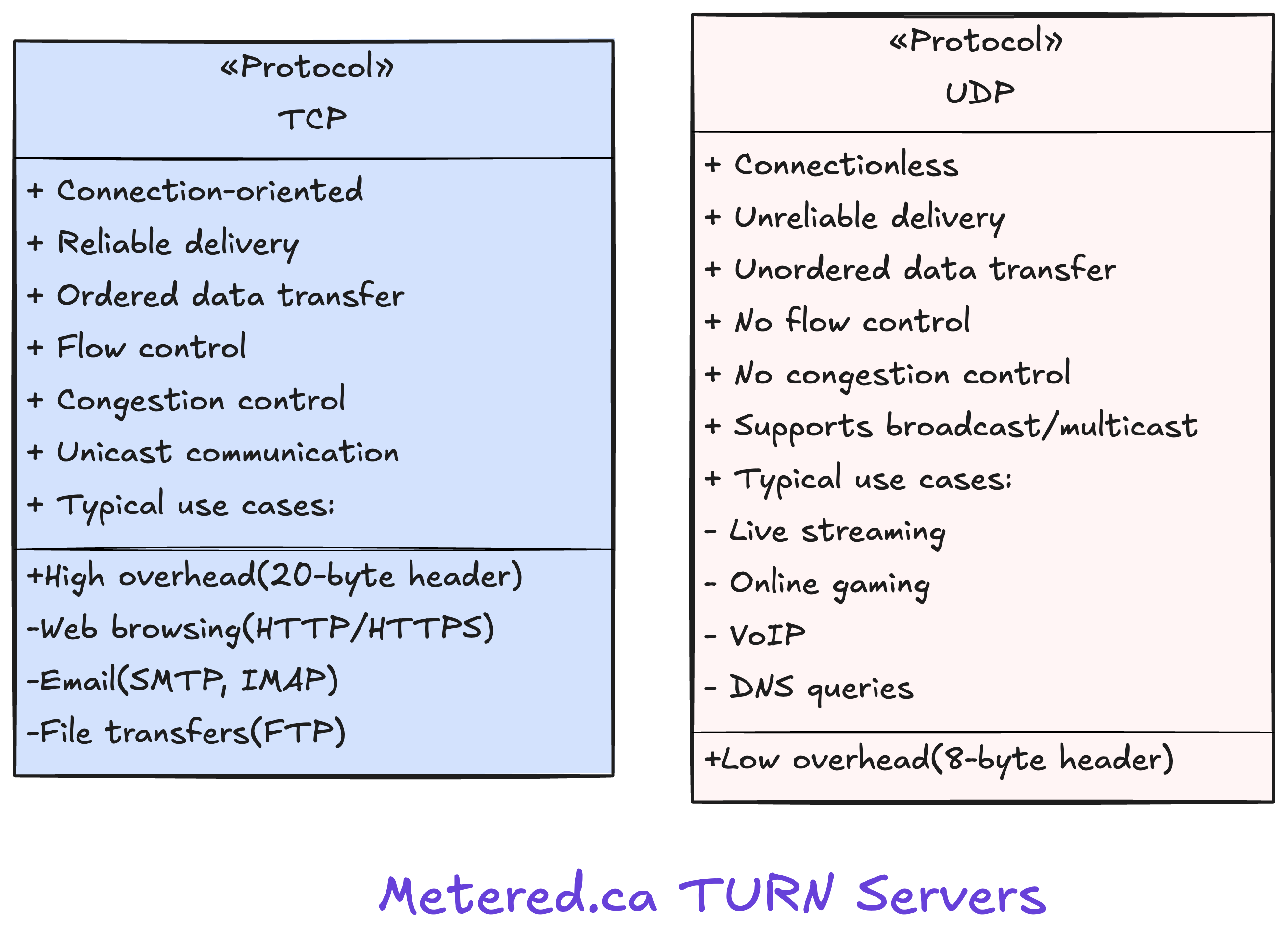
SMTP, or Simple Mail Transfer Protocol, is the standard protocol used for sending email messages between servers. It defines the format and transmission method for emails during the sending process. When you send an email, your email client typically sends it to an SMTP server, which then relays it to the recipient's SMTP server. SMTP is primarily a 'push' protocol, meaning it's used for sending mail, while other protocols like POP3 or IMAP are used for retrieving mail.
7. FTP (File Transfer Protocol)
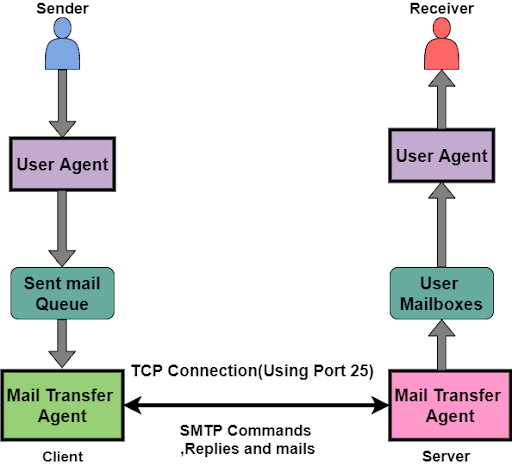
FTP, or File Transfer Protocol, is a standard network protocol used for transferring computer files between a client and server on a computer network. It operates on the application layer of the OSI model and the fourth layer (application layer) of the TCP/IP model. FTP uses TCP for data transfer, ensuring reliable and connection-oriented communication. Before a client and server can exchange files, they establish a connection through a "three-way handshake" process, guaranteeing a reliable connection. FTP is widely used for uploading and downloading files, maintaining websites, and transferring large datasets.
Conclusion
Internet protocols are the backbone of modern digital communication, each serving a unique and vital role. From the fundamental request-response mechanism of HTTP to the secure and encrypted connections of HTTPS, the reliable data transfer of TCP, the speed-optimized approach of UDP, the real-time capabilities of WebSocket, the email handling of SMTP, and the file transfer efficiency of FTP, these protocols collectively enable the seamless and diverse functionalities of the internet. Understanding these protocols provides a deeper appreciation for the intricate workings of the digital world we inhabit.




